- Stunnel Mysql Login
- Stunnel Mysql
- Stunnel Mysql Example
- Stunnel Mysql Configuration
- Stunnel Mysql Tutorial
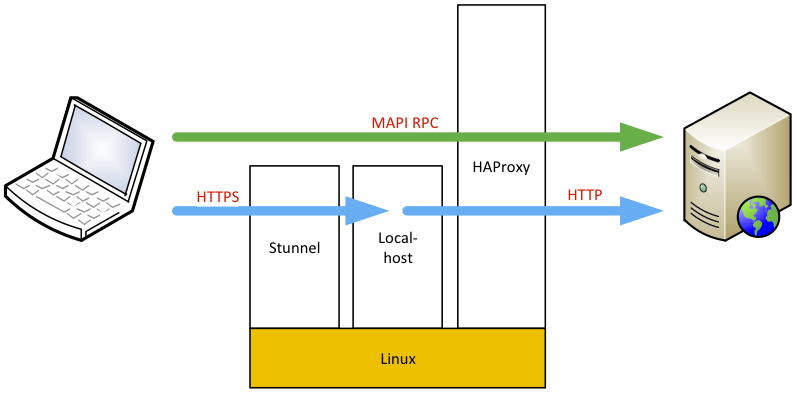
What's Stunnel
The Stunnel program is designed to work as an SSL encryption wrapper between remote client and local (inetd-startable) or remote server. It can be used to add SSL functionality to commonly used inetd daemons like POP2, POP3, and IMAP servers without any changes in the program's code.
What Stunnel basically does is that it turns any insecure TCP port into a secure encrypted port using OpenSSL package for cryptography. It's somehow like a small secure VPN that runs on specific ports.
Step 1: Update and Upgrade Ubuntu
Stunnel Mysql Login
Stunnel is a SSL proxy designed to add TLS encryption to existing clients and servers without changes to the daemon's themselves. One (or more) endpoint is run in server mode, the other endpoint is run in client mode. SSL in MySQL 5.6. The documentation for SSL in MySQL 5.6 is quite detailed, and it explains how SSL works. But first let's make one thing clear: MySQL supports secure (encrypted) connections between clients and the server using the TLS (Transport Layer Security) protocol. TLS is sometimes referred to as SSL (Secure Sockets Layer), but MySQL. MySQL SSL Certificates - works just like normal SSL. Can use client certificates to prevent unauthorised connections. No persistent connections with our existing setup. Still have to have MySQL listening on an open port on the firewall. Set up a port to port ssl tunnel. Do not have to reconfigure MySQL. For example, to connect to the MySQL server using the command line mysql client you would issue: mysql -u MYSQLUSER -p -h 127.0.0.1. Where MYSQLUSER is the remote MySQL user having privileges to access the database. When prompted, enter the MySQL user password. To terminate the SSH tunnel type CTRL+C in the console where the ssh client is. Using Stunnel to Secure MySQL Database Stunnel is a program that allows you to encrypt arbitrary TCP connections inside SSL. Stunnel can also allow you to secure non-SSL aware daemons and protocols (like POP, IMAP, LDAP, etc) by having Stunnel provide the.
Using these commands update your Ubuntu's package list and also upgrade the existing packages to the latest version:
Step 2: Install Stunnel on your VPS
Install Stunnel package using the code below:
Stunnel Mysql
Step 3: Configure Stunnel on the VPS
Stunnel configures itself using a file named 'stunnel.conf' which by default is located in '/etc/stunnel'.
Create a 'stunnel.conf' file in the '/etc/stunnel' directory:
We're going to be using a SSL certificate to identify ourselves to the server so we have to set the path to that certificate in 'stunnel.conf' file using this line (We will create the certificate file in the next step):
Next we specify a service for use with Stunnel. It can be any of the services which use networking such as mail server, proxy server, etc.
Here as an example we're going to secure traffics between Squid proxy server and a client using Stunnel. We'll explain how to install and configure Squid in Step 6.
Stunnel Mysql Example
After setting a name for the service you're going to use, you must tell Stunnel to listen on which port for that service. This can be any of the 65535 ports, as long as it's not blocked by another service or firewall:
Then depending on the service you're going to use the secure tunnel on, you must specify the port and IP address of that in the configuration file Basically Stunnel takes packets from a secure port and then forwards it to the port and IP address of the service you specified.
Squid proxy by default runs on localhost and port 3128 so we have to tell Stunnel to forward accepted connections to that port:
connect = 127.0.0.1:3128
So overall the 'stunnel.conf' file must contain the lines below:
Note: The client = no part isn't necessary, Stunnel by default is set to server mode.
Step 4: Create SSL Certificates
Stunnel uses SSL certificate to secure its connections, which you can easily create using the OpenSSL package:
Basically, the commands above is for creating a private key, creating a certificate using that key and combining the two of them into one files named 'stunnel.pem' to use with Stunnel.
Note: When creating the certificate, you will be asked for some information such as country and state, which you can enter whatever you like but when asked for 'Common Name' you must enter the correct host name or IP address of your droplet (VPS).
Also, enable Stunnel automatic startup by configuring the '/etc/default/stunnel4' file, enter command below to open the file in text editor:
Stunnel Mysql Configuration
And change ENABLED to 1:
Finally, restart Stunnel for configuration to take effect, using this command:
Step 5: Install Squid Proxy
Install Squid using the command below:
Step 6: Configure Stunnel in Client
Note: This explains the process of installing and configuration of Stunnel as a client in Windows, but Stunnel could also be installed in Linux and even Android and configuration still remains the same. The only difference would be placement of 'stunnel.conf' file required for configuration of Stunnel.
In order for Stunnel to communicate with the server, the SSL certificate we created in Step 5 must be present at the client. There are many ways of obtaining the 'stunnel.pem' file from server, but we're going to use SFTP which is both easy and very secure.
Using a SFTP client such as Filezilla, connect to your server and download the 'stunnel.pem' file located in '/etc/stunnel/' directory to the client.
Step 6: Configure Stunnel in Client
Note: This explains the process of installing and configuration of Stunnel as a client in Windows, but Stunnel could also be installed in Linux and even Android and configuration still remains the same. The only difference would be placement of 'stunnel.conf' file required for configuration of Stunnel.
In order for Stunnel to communicate with the server, the SSL certificate we created in Step 5 must be present at the client. There are many ways of obtaining the 'stunnel.pem' file from server, but we're going to use SFTP which is both easy and very secure.
Using a SFTP client such as Filezilla, connect to your server and download the 'stunnel.pem' file located in '/etc/stunnel/' directory to the client.
Install Stunnel in any place you like. Then go to the Stunnel folder and move the downloaded certificate'stunnel.pem' to Stunnel folder.
Stunnel Mysql Tutorial
Create a 'stunnel.conf' file in the Stunnel's folder if one does not exist. Open the file with a text editor such as Notepad.
First of all, we tell Stunnel our certificate's path, which in Windows is in the Stunnel's directory (reminder: in Ubuntu it is in '/etc/stunnel/' directory):
Since we are going to set up a client, we have to tell Stunnel that this is a client. Put the line below in the configuration file:
Then just like the server, we must specify configuration of the service we want to use.
First we specify the service's name, then the IP address and port, which Stunnel should listen to on the client:
The accept port could be any port on the client computer, as long as it's not occupied by another service or blocked by a firewall.
Next, we tell Stunnel to forward packets coming to this port to our Stunnel server's IP address and port. The IP address is your server's (droplet) public IP address, which is assigned to you when setting up a droplet, and port is the port you specified when configuring Stunnel in the server. In our case it was 8888 so we're going to tell Stunnel to connect to that port:
So the final 'stunnel.conf' file in the client should look like this:
Save and close the file and run 'stunnel.exe'.
That's it. Now our client is configured to communicate securely with the virtual server using a secure SSL tunnel. From now on when trying to connect to any service on our VPS, instead of connecting directly to IP address of server, we must use the IP address and port specified in the Stunnel's 'accept' part of configuration for each service.
As an example, when we want to connect to Squid proxy on our cloud server, we must configure our client to connect to 127.0.0.1:8080, and Stunnel automatically connects us through a secure tunnel to the service specified for that port. Here you can configure your web browser to use IP 127.0.0.1 and port 8080 as a proxy to secure your web traffic.
Date: September 18, 2014 05:41AM
The standard mysql ssl connection works:
mysql -h -u -p --ssl-key=/client-key.pem --ssl-cert=/client-cert.pem
Stunnel connection doesn't work:
mysql -h 127.0.0.1 -u -P 3307 -p --ssl-key=/client-key.pem --ssl-cert=/client-cert.pem
with stunnel.conf:
-------------------------------------
client = yes
pid = /etc/stunnel/stunnel.pid
debug = 7
output = /var/log/stunnel/stunnel.log
TIMEOUTclose=10
sslVersion = all
#options = NO_SSLv2
[mysqls]
accept = 127.0.0.1:3307
connect = :3306
----------------------------------
(I tried with or without 'options = NO_SSLv2')
I ask for your help to find what is wrong.
Thanks
Content reproduced on this site is the property of the respective copyright holders. It is not reviewed in advance by Oracle and does not necessarily represent the opinion of Oracle or any other party.

